In order to protect against ransomware attacks, you need to implement a sophisticated solution that includes a sure path to recovery.
Cybersecurity
Hackers Attacking International Suppliers
Cybercrime exploiting vulnerabilities in international supplier's networks There’s a saying, “Make sure everybody in your boat is rowing and not drilling holes when you’re not looking.” It’s a great analogy for some of the more recent high-profile incidents of...
Ransomware: What You Need to Know Now
Get Beyond Malware Attacks The internet is an amazing, useful and often wonderful thing. It’s also a giant mess. For every resource it gives your business that helps you succeed, it also offers a threat. Not-safe-for-work embarrassments aside, there are some...
The worst cyber security breaches of 2018 – Under Armour
Fitness apparel manufacturer Under Armour gave us a good example of how companies can try to protect their user’s data but often fail to fully cover everything that needs protecting. The information that was stolen from Under Armour is minor compared to some of the...
Worst Cybersecurity Breaches – VPNFilter
More and more, our business environments are connected to the cloud. The transmission of data and the speed to which it can be accessed is critical to business intelligence and competitive advantage. When that data becomes attractive to hackers, the vulnerability also...
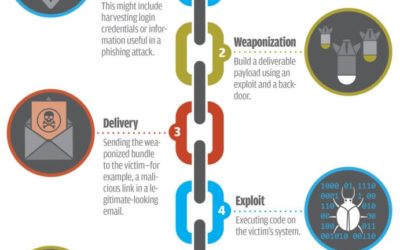
What is the Cyber Kill Chain?
The Lockheed Martin Kill Chain Lockheed Martin, known for defense and security technologies, among other things, has developed a new “kill chain” method of describing each stage of a cyber attack. Although cyber-attack chains may take different forms, these steps...
The Atlanta Ransomware Attack
The recent cyber attack on the municipal systems at the city of Atlanta shows the vulnerability of city governments
In the Mind of the Hacker
It’s impossible to put a number on how many “hackers” there are in the world, but the FBI has a list of their most wanted cyber criminals.
IRS Warning about CPA Firm Data Loss
No one likes a warning from the IRS, but CPA firms are taking heed of the most recent message from the stalwart government agency: “Step Up” security for the mountains of sensitive information you obtain each year. CPA firms regularly keep digital files of names,...
Don’t Let the Reaper Get Your Data
According to an article in the Wall Street Journal concerns are escalating over one of North Korea’s three major hacking organizations because of both their adeptness and sheer brazenness. APT37 aka “Reaper,” is a hacking group best known for attacking South Korea but...