The following post is a summary of a blog article published by our cybersecurity partner BitLyft with additional comments by this author.
We have all seen the popularity of TikTok explode in recent months, perhaps due to shelter-in-place orders and people tending to be more isolated due to COVID-19. It quickly became a preferred method of interaction for social media, and people are making money for video views, similar to how YouTube works. The app has algorithms to suggest and target content based on your likes and dislikes, allowing content to “go viral” quickly. Among social media influencers, this is huge.
Is TikTok spyware?

TikTok was especially popular in India, until the country recently banned it and 58 other Chinese-owned apps, while China and the United States still measured over two hundred million downloads. Given the widespread adoption, security concerns became more widespread. The data types and amounts collected are the basis of security concerns, but the app is in the same league as other US-based apps when it comes to collecting data. Generally, it collects device type and operating system, location data, and video history, although a Wall Street Journal investigation alleged it collected MAC addresses and other device identifiers. One important “feature” was the app’s ability to access the clipboard—the copy/paste function—in order to prevent users from spamming comments across multiple videos. This presented a significant security risk and was later disabled.
Is the TikTok threat real or political?
Much of the concern around TikTok is speculative and not necessarily based on factual evidence; however, we know the concerns are real. Most people who use TikTok probably are unconcerned with the information gathered after they install the app. Those casual users who are more concerned with the collection and dissemination of their info can simply not install/uninstall the app.
Given that the parent company of TikTok (ByteDance) is under Chinese control, we can speculate that the Chinese government could use the data for espionage or political gain. Since we have no evidence this has occurred, we cannot say for sure it is an issue.
A letter from Senators Tom Cotton (R-Arkansas) and Chuck Schumer (D-New York) revealed some significant concerns. First and foremost, they stated that “While the company has stated that TikTok does not operate in China and stores U.S. user data in the U.S., ByteDance is still required to adhere to the laws of China. Security experts have voiced concerns that China’s vague patchwork of intelligence, national security, and cybersecurity laws compel Chinese companies to support and cooperate with intelligence work controlled by the Chinese Communist Party.”
Additionally, “Questions have also been raised regarding the potential for censorship or manipulation of certain content…The platform is also a potential target of foreign influence campaigns like those carried out during the 2016 election on U.S.-based social media platforms.”
Since U.S. businesses are responsible for the security of their devices, networks, and data, many have blocked or mandated the removal of TikTok from any company device or platform. This is not an unusual practice for social media applications or non-business-related uses, and businesses must remain vigilant.
Utilization of a cloud backup provider such as Global Data Vault is an excellent way to add additional layers of protection to your company and significantly lower your risk of data exposure. Our Backup-as-a-Service offering is supplemented with BitLyft security to stay one step ahead of security threats to your environment.
More Cybersecurity Posts
Ransomware: What You Need to Know Now
Get Beyond Malware Attacks The internet is an amazing, useful and often wonderful thing. It’s also a giant mess. For every resource it gives your business that helps you succeed, it also offers a threat. Not-safe-for-work embarrassments aside, there are some...
The worst cyber security breaches of 2018 – Under Armour
Fitness apparel manufacturer Under Armour gave us a good example of how companies can try to protect their user’s data but often fail to fully cover everything that needs protecting. The information that was stolen from Under Armour is minor compared to some of the...
Worst Cybersecurity Breaches – VPNFilter
More and more, our business environments are connected to the cloud. The transmission of data and the speed to which it can be accessed is critical to business intelligence and competitive advantage. When that data becomes attractive to hackers, the vulnerability also...
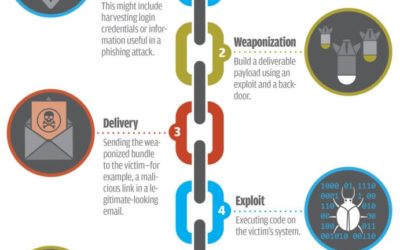
What is the Cyber Kill Chain?
The Lockheed Martin Kill Chain Lockheed Martin, known for defense and security technologies, among other things, has developed a new “kill chain” method of describing each stage of a cyber attack. Although cyber-attack chains may take different forms, these steps...



0 Comments