Data Backup
A data backup solution protects your company from attack by hackers and from natural disasters as well as facilitates speedy recovery and fast failover times.
The Importance of a Data Retention Policy and Scheduled Backups
A strong data retention policy and scheduled backups are important to maintain the security of data and ongoing commercial operations.
Cybersecurity Guide for Cloud Data Management
Not only must companies protect edge-facing and core-facing infrastructure technologies, they must protect all data at all times, and in all locations.
Next Level Backup Protection
Physical and logical security are two important factors when considering backup files. Modern restore capabilities allow for entire virtual machines and systems to be brought back online from a backup very quickly, assuming that a local/on-premises version is...
Veeam Availability Suite v10 has impressive new capabilities
Veeam Backup & Replication v11 is Here! The V11 update was released in March 2021. As usual, the list of new features is extensive. Click through for a post in which we focus on the new capabilities that are important to Global Data Vault, our partners, and our...
Cloud Mobility – Buzz Words or Pain Point?
Do an internet search on “cloud mobility,” and you will get a TON of results. The definition(s) can be confusing, but basically it describes the ability to avoid locking in workloads to a specific cloud vendor. Diversification of resources between private and public...
The Air Gap Controversy
In a previous blog post, we talked about the 3-2-1-1 data protection concept as well as “air gaps.” We’ve also discovered that viruses can corrupt files that are written to air-gapped technologies, such as tape, rendering them useless, and the same can happen to other...
Gartner Magic Quadrant for Data Center Backup and Recovery
Veeam Software is an unusual participant in the Gartner Magic Quadrant given that they entered it in the visionary section, and were the first company to do so with only a virtualization offering.
What is Global Data Vault’s Enhanced Data Protection?
In Veeam Backup and Replication 9.5 Update 3, Veeam introduced a feature called “Insider Protection,” and updated it for the most recent release of Update 4. Insider Protection is a method used to combat the malicious or intentional (and perhaps even accidental)...
Adding an Air Gap to the 3-2-1 Backup Rule
It’s not a matter of IF your business will succumb to hackers, a natural disaster, employee theft or other mismanagement of data. It’s a matter of WHEN. Naturally, it’s become common practice to keep safe backups of anything business essential, but how companies keep those backups varies considerably.
Worst Cybersecurity Breaches – VPNFilter
More and more, our business environments are connected to the cloud. The transmission of data and the speed to which it can be accessed is critical to business intelligence and competitive advantage. When that data becomes attractive to hackers, the vulnerability also...
Bandwidth – How Much is Enough?
Knowing and planning for an appropriate level of bandwidth is a key component of every DRaaS solution. In our most common DRaaS implementation, the data is moved from local repositories at the customer site over the internet or WAN to our data centers once per day,...
Sizing for Local Backup Repositories
Sizing Local backup RepositoriesProper sizing for local backup repositories is a critical step in building a complete backup and disaster recovery as a service solution (DRaaS). Below, we will list the most accurate way of determining what your data change rate is and...
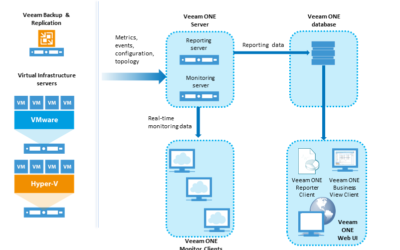
What is Veeam Backup
What is Veeam Backup? If you rely on virtualization then older backup and DR solutions that used to work effectively may no longer do the trick…
What is Cloud Disaster Recovery (Cloud DR)?
What Is Cloud Disaster Recovery? Often shortened to Cloud DR, disaster recovery is a plan put into place in case a disaster hits. Cloud DR refers to the component in your disaster recovery plan that involves the use of a cloud backup environment. The Cloud Component...
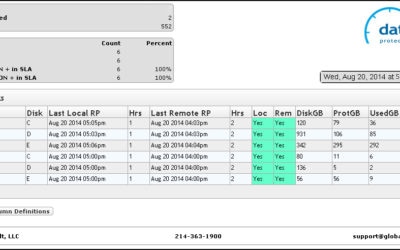
Data Protection Dashboard Provides Easy to Use Status Window
Global Data Vault Web Portal At Global Data Vault, we ensure the quality of your recovery environment through constant monitoring. Nothing is more important to your business operations than your data and the systems that support it. Not only do we monitor your...
Developing a Data Retention Policy: What to include in your data backup?
(The second in three part series on Developing an Effective Data Retention Policy. In our previous article, Developing an Effective Data Retention Policy, we outlined the history of and comparison of tape backup environments to disc backup environments. Understanding...
Data Backup: Developing an Effective Data Retention Policy
(The first in a three part series. Jump to Part Two: What do you HAVE to back up?) Archiving one’s data is a challenge for every business, whether the business is a billion dollar enterprise or a SOHO. Data loss can be devastating to the profitability of any...
Your Data – Making Sure It’s Protected
Computer hardware fails, and the result is often the loss of valuable data. At Global Data Vault, we have a front-row seat to this mayhem. To ensure your offsite backup solution provides recovery as you expect, you must make sure that all of your important data is...
Why Do Disk Drives Fail
Global Data Vault is inherently interested in data protection and providing disaster recovery solutions for when disk drives fail. Continuing in our series of weighing the differences between enterprise class disk drives and desktop class disk drives, we are now...
Backup Tips – 12 Things You Must Backup
There will come a time in your business life where you either have a computer crash, a large scale network disaster or you have to reinstall an operating system. In any of those dreaded events, you will thank your lucky stars if you have followed these computer backup...